How Open Source Evidence was Upheld in a Human Rights Court
Many questions remain as to how open-source data can be used or presented in court as evidence.
The field of open source investigations is still relatively new in the grand scheme of things, after all. But with the ongoing war in Ukraine presenting a mountain of open source data for prosecutors to work with, understanding those questions and how they can be answered is of vital importance.
A recent decision at the European Court of Human Rights (ECHR) on the case of Ukraine and The Netherlands vs Russia (applications nos. 8019/16, 43800/14 and 28525/20) provides some insight into how such evidence may be treated and the challenges it could face.
The ECHR is an international court of the Council of Europe that looks to interpret the European Convention on Human Rights, while the case brought by Ukraine and the Netherlands sought to prove human rights violations in areas of Ukraine occupied by Russia since 2014.
Among the evidence presented by lawyers representing Ukraine were details from research and articles compiled by Bellingcat and others on topics such as Russia’s involvement in Ukraine, the fate of MH17, cross-border artillery attacks and the operation of Russian army personnel in eastern Ukraine.
Lawyers representing Russia sought to undermine open source evidence that had been presented.
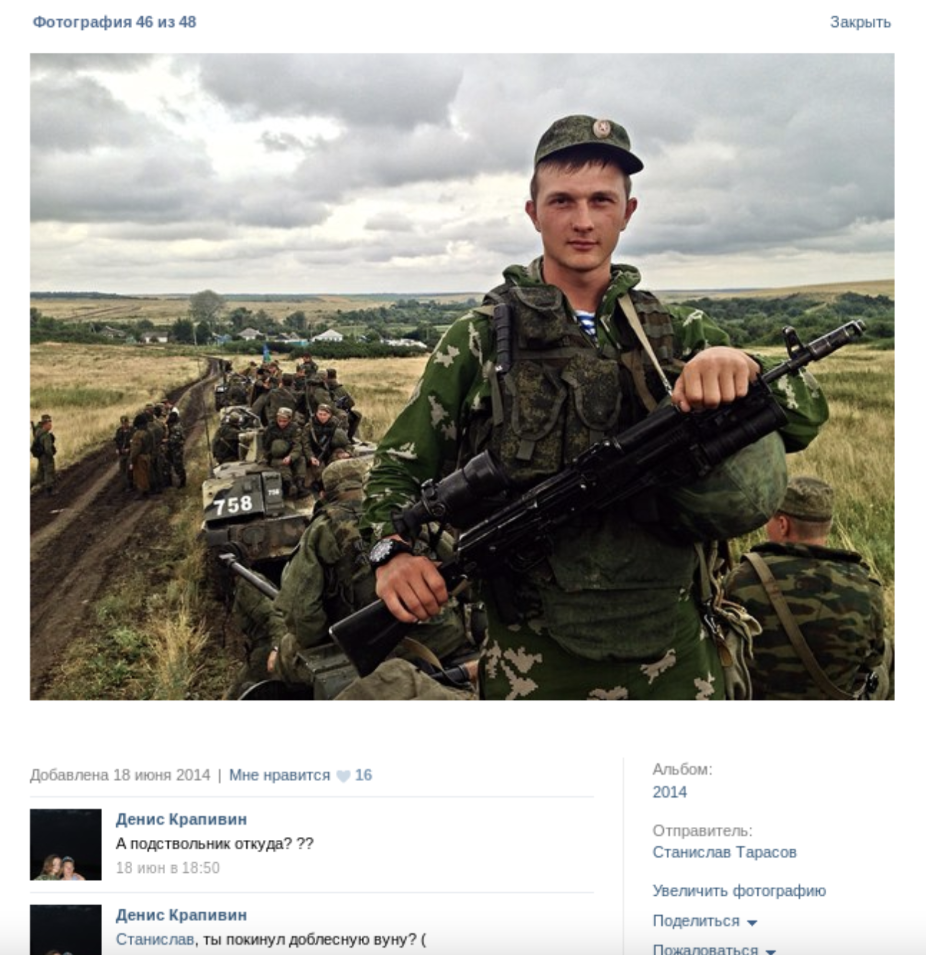
This included questioning whether photographs that appeared to show a Russian soldier standing in front of a vehicle in southern Russia had been manipulated.
Questioning the Authenticity of an image
The photographs were used by Bellingcat in an article to demonstrate an exercise in geolocation, placing the soldier in a training field near the border with Ukraine.
The image was important in the ECHR case as it had allowed researchers to place the individual pictured, and therefore his military unit, at the Pavloka Training Camp near the Ukrainian border. Pavloka was the site of artillery strikes into eastern Ukraine in 2014.
However, an image posted in the Bellingcat article appeared to contradict a similar picture presented by the Atlantic Council Think Tank on page 23 of this report.
In the Atlantic Council version of the image, a number appeared on a military vehicle behind the soldier. This number was not present on the image detailed in the Bellingcat article that was published.

Russia’s representative at the ECHR claimed that this discrepancy showed the Bellingcat image had been manipulated using very “sophisticated” techniques and “artificial intelligence”. This ensured what had been presented to the court was little more than “propaganda”, they stated.
Explaining how this discrepancy came about, and proving that there was nothing untoward, was key to ensuring this particular piece of open source evidence – and open source investigations more broadly – were seen as reliable in the eyes of the court.
Checking the Archives
It is evidently correct to state that the numbers visible on the vehicle are missing in one of the images. But the claim it had been purposely manipulated by Bellingcat was untrue – as further open source evidence showed.
Firstly, the intent of the Bellingcat article was to offer a case study on geolocation – as is clear from the article’s title. It did not look to address why the numbers on the vehicle had appeared in some images but not in others. Yet given the point was raised by Russia’s representative, it had to be addressed.
It transpired that many of the original posts and links used in the geolocation and Atlantic Council report were no longer live, deleted by the user or made private.
Fortunately, the links had been archived by researchers using sites like archive.org and archive.today. This ensured early versions of the pages where the images appeared could be provided to the court – a useful reminder to researchers of why it’s vital to archive as much as possible during the research process.
For example, a LiveJournal blog from August 2014 contained screenshots of the version of the photograph that displayed the numbers on the vehicle that had been taken from the soldier’s VK page. The blog also showed that this image had been posted in mid-2014. This was the version of the photograph used in the Atlantic Council report.
A further archived tweet from July 2014 included a screenshot of the soldier’s social media post featuring the photograph displaying the number on the vehicle.
Yet other archived images showed the vehicle with no number.
This was the case in this December 2014 post from the soldier’s own VK page. However, a close inspection showed that the image appeared to have been rather crudely photoshopped, with the section where the number was appearing blurry.
Looking more closely at the archived images, it seemed apparent that the first versions of the image showed the numbers on the vehicle but at some point in 2014 newer photos without the numbers began to be posted online.
The key piece of evidence that allowed the full picture to become clear was another archived version of the soldier’s VK.com page that shows he “updated his profile picture” with the edited image on 23 December, 2014.
All this appeared to show that the soldier had in fact posted the altered version of the photograph on his social media profiles after previously posting the original with the number on the vehicle several months earlier.
A footnote in the Atlantic Council report even detailed that the soldier had posted the photo, then deleted it before uploading it again in late December 2014.
The implication that Bellingcat was involved in the manipulation of the photo was clearly untrue, evidenced with publicly available open-source material.
The court agreed, stating that it did not “accept that these criticisms show any general tendency to manipulate evidence or any general flaws in the analysis or approach taken by the authors of the reports.” Its full response can be read here.
Proving the Worth of Open Source Material
Russia’s representatives also questioned the credibility of open source investigators in general.
The strategy for doing so appeared clear when they claimed that the work of the Joint Investigation Team (JIT) in the MH17 trial had relied on “dubious digital material and reports from “so-called” citizen journalists”.
Such material they claimed again “was susceptible to manufacture or manipulation”. The techniques for doing so “were now so sophisticated that false material was virtually undetectable,” they stated.
It seemed that Russia’s representatives thought if they could undermine open source evidence provided by the likes of Bellingcat and other independent actors, they could then conflate that with contributions from the JIT and sow doubt about the credibility of the criminal investigation into the downing of Flight MH17.
However, the ECHR did not buy this argument either.
In its decision it stated that:
“First, there is no evidence that the JIT has relied upon outside bodies, including Bellingcat, in its analysis of the material and the preparation of the criminal case-file. Rather, it is absolutely clear from the submissions that the JIT has conducted its own analysis in respect of all the evidence in the criminal case-file, including issues discussed in Bellingcat reports and the matters covered by the DSB [Dutch Safety Board] report. There is no basis whatsoever for suggesting that the OM and JIT material has not been independently gathered and authenticated. The fact that their conclusions are consistent with those of the DSB and Bellingcat merely demonstrates that there is corroboration of the conclusions reached and serves to further enhance the credibility and reliability of the findings.”
The decision also stated that it was “noteworthy” the JIT conclusions were consistent with those arrived at independently by Bellingcat and other open source contributors. This would “tend to lend support to the credibility of these findings and the methodologies followed”, the court stated.
Such conclusions are not only reassuring for researchers but serve as validation of their work. It also bodes well for organisations using open-source evidence and analysis to document incidents that may lead to human rights cases, prosecutions or trials.
This is particularly the case given the work of many organisations around MH17 was not designed with legal accountability in mind.
In the period since, legal scholars and organisations such as GLAN have worked with Bellingcat to design collection, analysis and archiving processes that operate to an evidentiary standard.
Such actions can only help ensure open source evidence will be accepted in future trials.
Bellingcat is a non-profit and the ability to carry out our work is dependent on the kind support of individual donors. If you would like to support our work, you can do so here. You can also subscribe to our Patreon channel here. Subscribe to our Newsletter and follow us on Twitter here.